In today’s world the most common external threat is Ransomware. In this document the steps to limit the risk of getting hit by a Ransomware attack are described. But first:
Ransomware is a business problem, not an IT problem. Responding to a Ransomware attack needs a business response, as responding to a Ransomware attack, WILL break things.
The top 5 MUST DO actions to limit the risk of a Ransomware attack are:
- Implement Multi Factor Authentication solution for ALL users on ALL external facing services.
- Patch, Patch, Patch and Patch!!!!
- Limit Privileged Access in your environment and practice least privilege for all other accounts.
- Use unique Local Admin password.
- Use Offline or WORM Back-ups for your key systems.
For the techies, let’s get into a bit more detail.
For the managers, go get the funding for the top 5 Must Do’s!!!
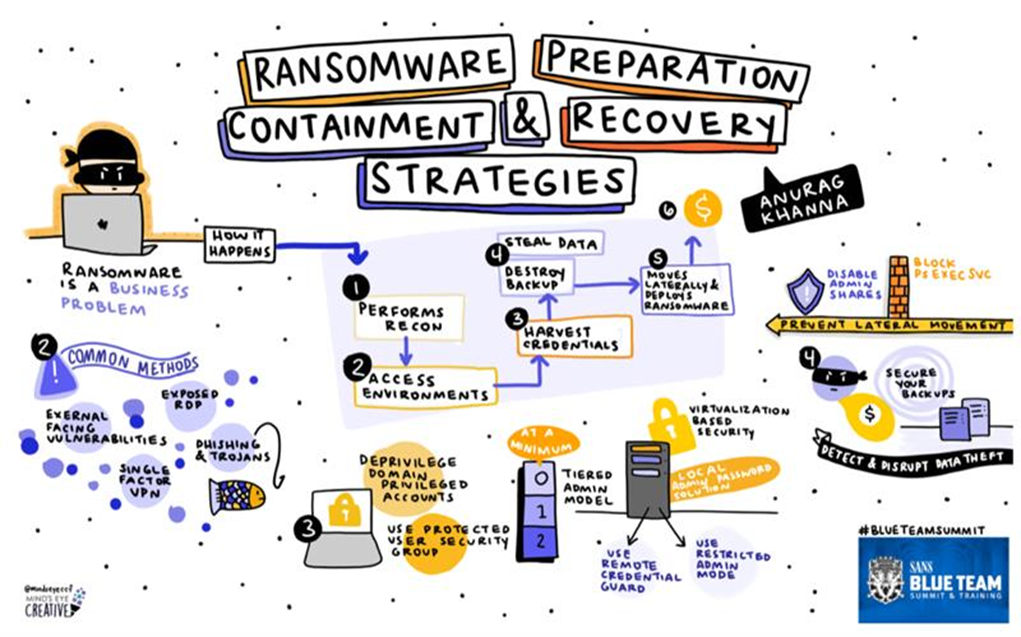
Threat Actor motivations and objectives.
The only motivation of the threat actor is: Getting paid!!!!
To reach this objective, the threat actor will try to:
- Infiltrate the infrastructure and systems.
- Escalate privileges.
- Destroy backups to make recovery harder.
- Exfiltrate critical data for extortion.
- Deploy Ransomware to system.
Anatomy of a Ransomware attack.
Let’s take a closer look at the anatomy of a Ransomware attack.
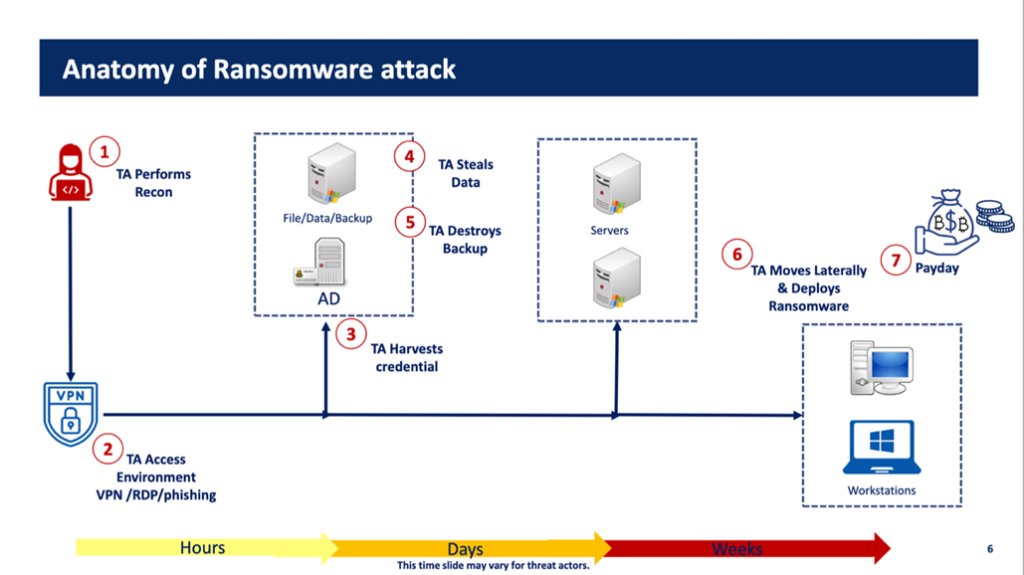
Source: Ransomware Preparation Strategies – Anurag Khana – SANS Blue Team Summit 2021
The Threat Actor will:
- Search for and collect information about the potentials target.
- Gain access by exploiting an initial vector.
- Dump credentials in the environment.
- Exfiltrated data for intimidation.
- Make the Back-ups useless.
- Move laterally and Push Ransomware to lock you out.
- Get paid :-> ‘Show me the money!’
Ransomware Attack phases
Now let’s take a look at each Threat Actor’s attack phase a bit deeper and see what we can do to make it harder for them.
Recon
The first phase is the reconnaissance of the target. The threat actor uses several tools and sources to investigate a target. Not much we can detect or do about this phase. We can make it harder for the threat actor. One of the actions we can do is blocking legacy authentication and protocols like IMAP and POP3. These protocols are used by the threat actor to verify stolen credentials.
Initial Compromise
After selecting a target, the threat actor will search for a way into the target infrastructure. The most commonly used entry points are:
- Publicly accessible services with known unpatched vulnerabilities.
- Exposed RDP.
- Phishing and Trojans.
- Single Factor VPN.
Let’s look at each of these entry points.
Publicly accessible services with known unpatched vulnerabilities
During the recon phase the threat actor will use tools to search for vulnerable system with an external Internet connection. Not much we can do about this. Well, we can! The first counter measurement is limiting the external facing services. Only connect systems to the Internet that cannot operate without this connection. Convenience is NO reason to connect a system to the Internet.
The biggest threat to Internet facing systems are unpatched known vulnerabilities. While these are easy to remediate: patch the system as soon as a security update or patch package is available. Each Internet connection should be monitored on network traffic and activities. You should also limit what information legitimate services expose publicly. For example, configure a service in such a way that it does not show the OS it is running on or the exact version of the service. While this is considered security through obscurity it does make it a little harder for an actor to get the information he or she needs.
Exposed RDP
We often see systems with an available Internet facing RDP connection. This should be limited. No system should have an Internet facing RDP connection unless no other options are available, and the RDP connection is absolutely necessary. Using a jump server to connect to other systems is preferred. Internet facing RDP connections should be secured by using an MFA solution. MFA exceptions for account should NOT be used. MFA for All.
Also make sure the Internet facing systems with RDP connections are always patched to the latest level and that all RDP connections are monitored. These recommendations also apply to exposed SSH and Telnet services.
Phishing and Trojans
Phishing and Trojans are two of the most used methods to gain credentials for the initial access to an environment. To protect an organization against phishing attacks, two important countermeasures can be used.
- Use Email Security Solution.
Services like Microsoft Defender for Office or Mimecast have highly intelligent options to detect phishing emails and URL’s. - User Awareness.
Some phishing campaigns are so sophisticated that they are able to bypass the Email Security Solutions. For this reason, your users should be trained on recognizing them. User Awareness programs like KnowBe4 can be implemented to train the end users is detecting phishing emails.
Trojans
Another method used by threat actors are Trojans. Trojans are little programs or code which trigger actions on a vulnerable system. Using the Trojans threat actors can install backdoors to get access to the infected system or harvest credentials of privileged accounts.
To protect systems against these Trojans the following measures can be taken:
- Disable Macro Execution.
Often Trojans are executed by hiding them in Macro’s in Office documents like Word and Excel. By disabling Macro execution in the programs, the Trojan installation will not start automatically. - Change default programs associated with vb, js, ps1.
By changing the default programs associated with known extensions, the malicious file will not be able to start the malicious payload. Instead, the content of the malicious file will be opened in, for example, notepad. This way the threat factor is reduced.
Single Factor VPN
Most organizations use some kind of VPN solution to provide external access to the infrastructure. To limit the threat of a Ransomware attack the following criteria must be met:
- Use MFA for ALL accounts on VPN.
- Force users to enter code rather than push notifications (Prevent MFA Fatigue).
- Disallow Privileged account use over VPN.
- Monitor VPN logons.
Threat Actor Harvests Credentials
After the threat actor has gained access to the target environment, the next phase is the harvesting of credentials. The three most used methods are:
- Use Mimikatz to dump credentials.
- Use Procdump to dump LSASS.
- Steal the NTDS.dit and extract the passwords.
A good Endpoint Security solution can detect these activities.
Domain Privileged Accounts
The threat actor will always be looking for Domain Privileged accounts. These accounts provide the easiest way to do lateral movement and execute malicious activities. Therefor the following statements should be true in the infrastructure:
- Deprivilege Domain Privileged Accounts.
- Enterprise Admins and Schema Admins security groups should ALWAYS be empty.
- Activate only when needed and remove when not applicable.
- Limit Domain Admin accounts.
- 90% of Domain Admin accounts can be set to Domain User with the correct additional permissions. Often third-party software ‘require’ these permissions. Well, they don’t. And when they really do, find other software.
- Backup Operators, Print Operators, Server Operators, Account Operators, DNS Admins, Group Policy Creator Owners should only be used when necessary.
- Enterprise Admins and Schema Admins security groups should ALWAYS be empty.
- Use Protected Users Security Groups.
- Requires minimal Domain Forest Level: Windows Server 2012.
If your Domain Forest Level is lower than Windows Server 2012, UPGRADE your Domain Controllers.
- Requires minimal Domain Forest Level: Windows Server 2012.
- Periodically review permissions for principals that can modify GPO’s and monitoring / auditing settings.
- Disable weaker Authentication mechanisms.
By default, all authentication mechanisms are enabled on the Domain. This is a high risk. Make sure only the authentication mechanisms that are used are enabled. Investigate why the weaker authentication mechanisms are enable and what use them. Then try to eliminate them by reconfiguring the systems or upgrading the software that use them.
Protect Privileged AD Credentials by using the Tiered Admin Model
The best way to protect our privileged accounts is by introducing the Tiered Admin Model. By using this model privileged accounts are never used on non-Tier 0 systems and harvesting them is much more difficult.
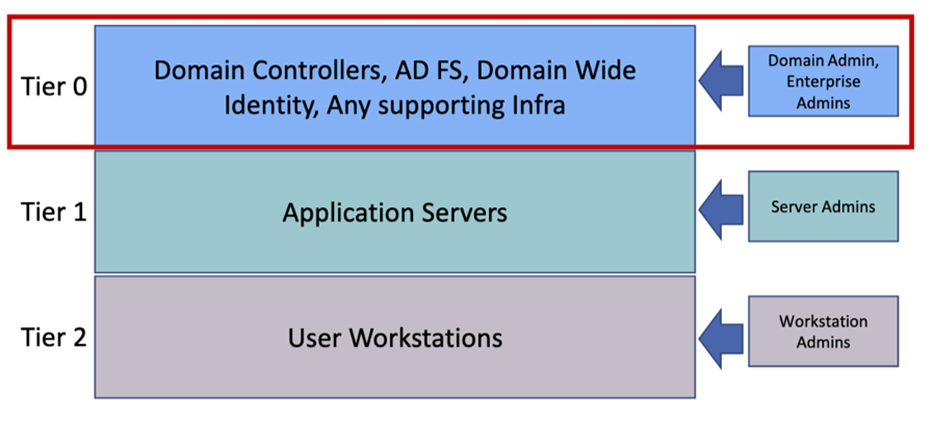
Tier 0 admins are allowed interactive logon to Tier 0 assets ONLY. By bare minimum, limit Domain level privileged accounts to Domain Controllers only. Make sure to enforce Logon restrictions to Privileged Accounts.
By using Group Policy, it is easy to set the Logon Rights restrictions for Tiered systems. Configure the following Group Policy options:
- Deny Access to this computer from the network.
- Deny logon as a batch job.
- Deny logon as a service.
- Deny logon locally.
- Deny logon through Remote Desktop.
When using Remote Administration on systems the following options can be used to harden these systems:
- Use Remote Credential Guard
- Protects privileged credentials when over RDP.
- Enables RDP connections without leaving credentials on the target system.
- Credentials remain on the source system. The target requests Service Tickets from the source system as required.
- Use Restricted Admin Mode
- Protects privileged credentials when over RDP.
- Solution for helpdesk support scenarios.
- Remote user requires admin privileges on target system.
Local Administrator account
Re-using the same Local Administrator password on systems is a big NO-NO. Threat Actors love these configurations as it makes lateral movement a piece-of-cake.
To prevent the re-usage of Local Administrator passwords, deploy Local Administrator Password Solution (LAPS)
- LAPS rotates passwords automatically and stores them in ‘ms-Mcs-AdmPwd’ attribute on the Domain Controller.
- LAPS ensures the correct Discretionary Access Control List (DACL) for the ‘ms-Mcs-AdmPwd’ attribute in the Domain Schema.
Protect the Local Security Authority (LSA)
Often credentials are harvested through the Local Security Authority (LSA). There are two options to make the LSA a bit more secure:
- Prevent reading memory and code injection by non-protected processes. (LSA Protection)
- Protected mode requires that any plug-in that is loaded into the LSA is digitally signed with a Microsoft signature.
- Audit mode can be used to detect access or precursor to moving to protection.
- Set Registry key: HKLM\SYSTEM\CurrentControlSet\Control\Lsa “RunAsPPL”=dword:00000001
- Use Credential Guard.
- Isolates secrets by using Virtualization based security.
- Has several hardware and software requirements.
Exfiltration
After setting up the infrastructure for the Ransomware attack, the threat actor will most likely start the exfiltration of data. To do so, a enormous number of tools are available. Among the most commonly used are:
- (s)FTP connections.
- File Sync applications. (MegaSync, rclone, pCloud, etc.)
- Remote Management tools. (AnyDesk, TeamViewer, etc.)
- Data compression tools. (zip, rar, 7zip, etc.)
Monitoring the installation and usage of these tools should be implemented. Tools like Windows Applocker and Microsoft Defender for Endpoint can help to give these insights.
Secure Back-ups
After collecting and extracting the business data, the threat actor will make sure the data cannot be restored using the back-up solution. To prevent the deletion / obstruction of back-ups the following actions can be taken:
- Limit the deletion of Volume Shadow copies.
- Back-up all critical systems required to run business.
- Protect back-ups against encryption / erasure.
- Back-up to Immutable storage. WORM (Write Once, Read Many)
- Use Offline Back-ups.
- Periodically test the back-ups.
Lateral Movement
Threat actors will try to infect as much systems as possible. To do so they must have a lateral movement method to connect to these systems. Commonly used literal movement methods are:
- SMB Shares
- PsExec
- RDP
- WMI
- Windows Remote Management (WinRM)
- Group Policy
To limit the lateral movement options, several measures can be taken.
Segment the network and endpoints
Segmentation at the network level gives you an incredible amount of control and makes it possible to reduce risk based on function of devices or on department of the organisation.
For example, segment all servers with the same function in their own subnets and restrict access by network ACL on the switch level and firewalls on the edge.
Segment client workstations based on business function (sales, marketing etc.) and do the same as above.
Besides segmenting the physical network, you can use the Windows Local Firewall to segment the infrastructure. This can be done by using Group Policies to enable and configure the Windows Firewall. Exceptions should only be created when needed and should be machine specific.
Commonly used Windows Firewall Rules:
| Protocol | Ports | Command Line |
| SMB | tcp/445, tcp/135, tcp/139 | Netsh advfirewall firewall set rule group=”File an Printer Sharing” new enable=no |
| RDP | tcp/3389 | Netsh advfirewall firewall set rule group=”Remote Desktop” new enable=no |
| WMI | Tcp/153, dynamic ports | Netsh advfirewall firewall set rule group=”Windows Management Instrumentation (wmi)” new enable=no |
| WinRm | Tcp/80, tcp/5985, tcp/5986 | Netsh advfirewall firewall set rule group=”Windows Remote Management” new enable=no |
Disable shares
Admin shares are often used to move laterally and copy tooling. You should disable the Admin Shares on system. Do NOT disable Admin Shares on Domain Controllers.
- Disable LanManServer service.
- Sc stop “LanManServer”
- Sc config “LanManServer” start=disabled
- Disable Shares using Registry
- Reg ADD
- HKLM\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters /v AutoShareWks/AutoShareServer /t REG_DWORD /d 0
Block PsExec
One of the commonly used application in lateral movement is PsExec. This command line application can be used to executed commands, create and start services. To prevent PsExec to execute these actions a fake PsExec Service can be created by using the following command:
Sc.exe create PSEXESVC start-disabled binpath=notepad.exe
Secure RDP
When RDP is used to connect between internal systems the following should be used.
- Use Remote Credential Guard
- Protects privileged credentials when over RDP.
- Enables RDP connections without leaving credentials on the target system.
- Credentials remain on the source system. The target requests Service Tickets from the source system as required.
- Use Restricted Admin Mode
- Protects privileged credentials when over RDP.
- Solution for helpdesk support scenarios.
Secure WMI
On systems where WMI is not required, remote access to remote WMI should be disabled by using the Window Firewall. The following Windows Firewall rule should be created:
| WMI | Tcp/153, dynamic ports | Netsh advfirewall firewall set rule group=”Windows Management Instrumentation (wmi)” new enable=no |
Secure Windows Remote Management (WinRM)
WinRM should only be available from trusted devices. Using the following command, the Windows Firewall rule can be created.
| WinRm | Tcp/80, tcp/5985, tcp/5986 | Netsh advfirewall firewall set rule group=”Windows Remote Management” new enable=no |
Group Policy
By using Group Policy, a threat actor can easily change security configurations or deploy tools or Ransomware. Permissions to create and edit GPOs should be set to the minimal required persons and periodically being reviewed. Creation of and changes to GPOs should be continuously monitored and audited.
When using the Tiered Admin Model, GPOs should only be targeting a specific Tier. Using a GPO across Tiers should NOT be used.